Integrating Darktrace with FA&I
Integrating Darktrace with FA&I to perform forensic investigations
- To integrate the two platforms, please follow the previous document here to log into the FA&I instance and create an API key. Select
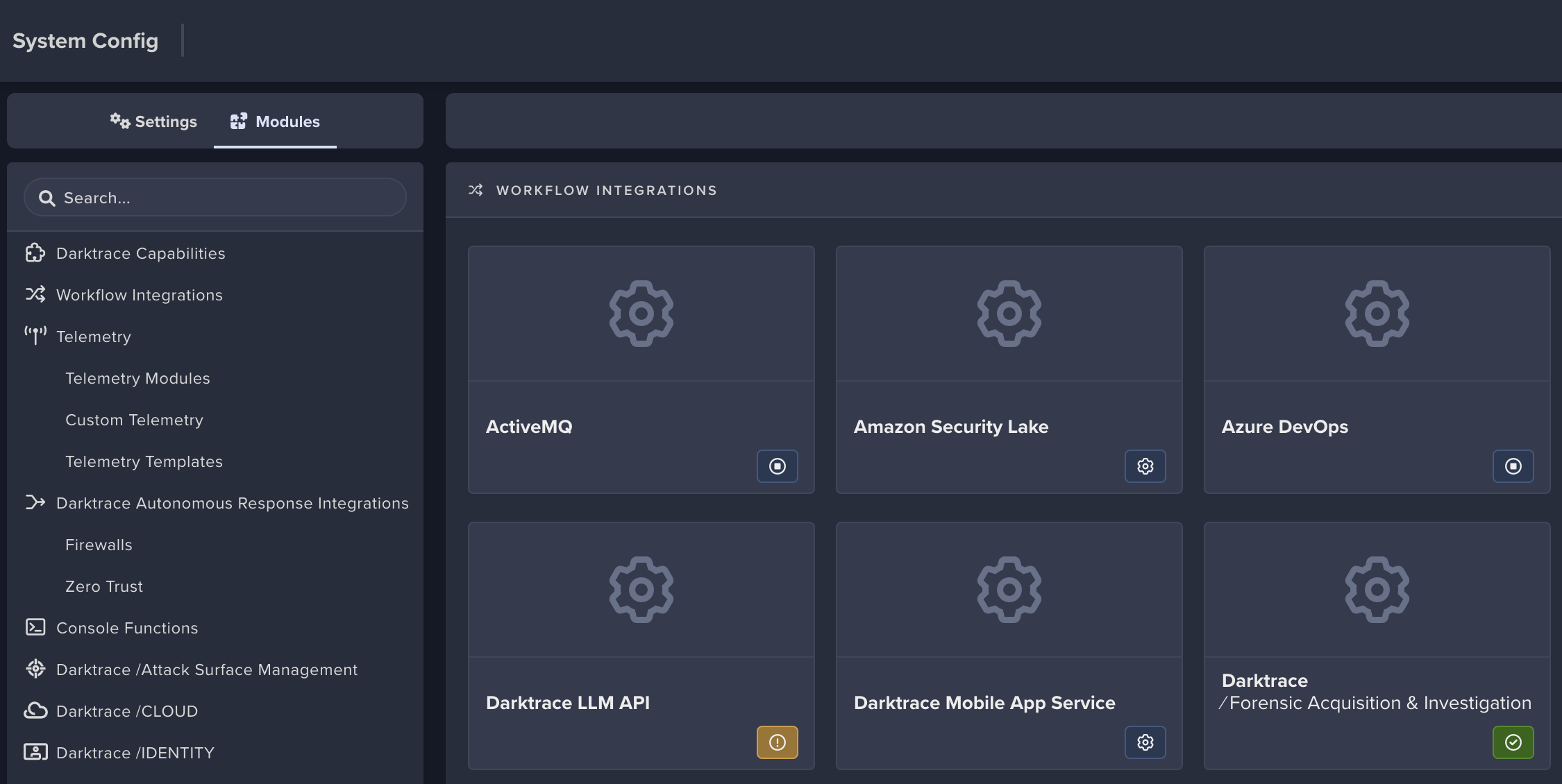
Darktraceas the role. - In Darktrace Threat Visualizer screen, navigate to System Config > Modules (/system-config#modules)
- Select
Modules,Workflow Integrationsthen click onDarktrace /Forensic Acquisition & Investigation
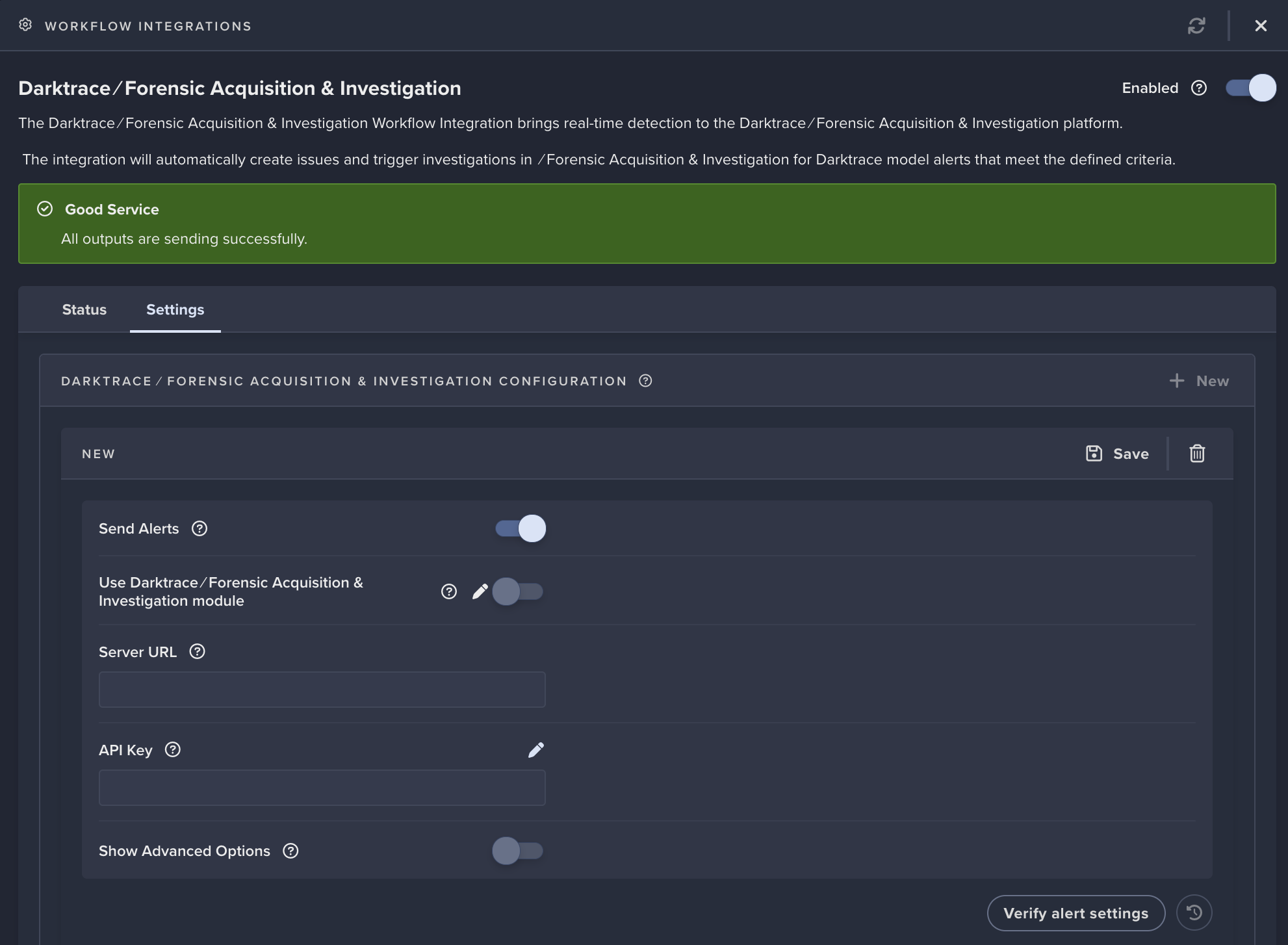
- Make sure the Integration is
Enabledthen click on+ New - Ensure 'Send Alerts' is enabled, and insert the URL for the FA&I SaaS instance and the Darktrace role API key that you have just created
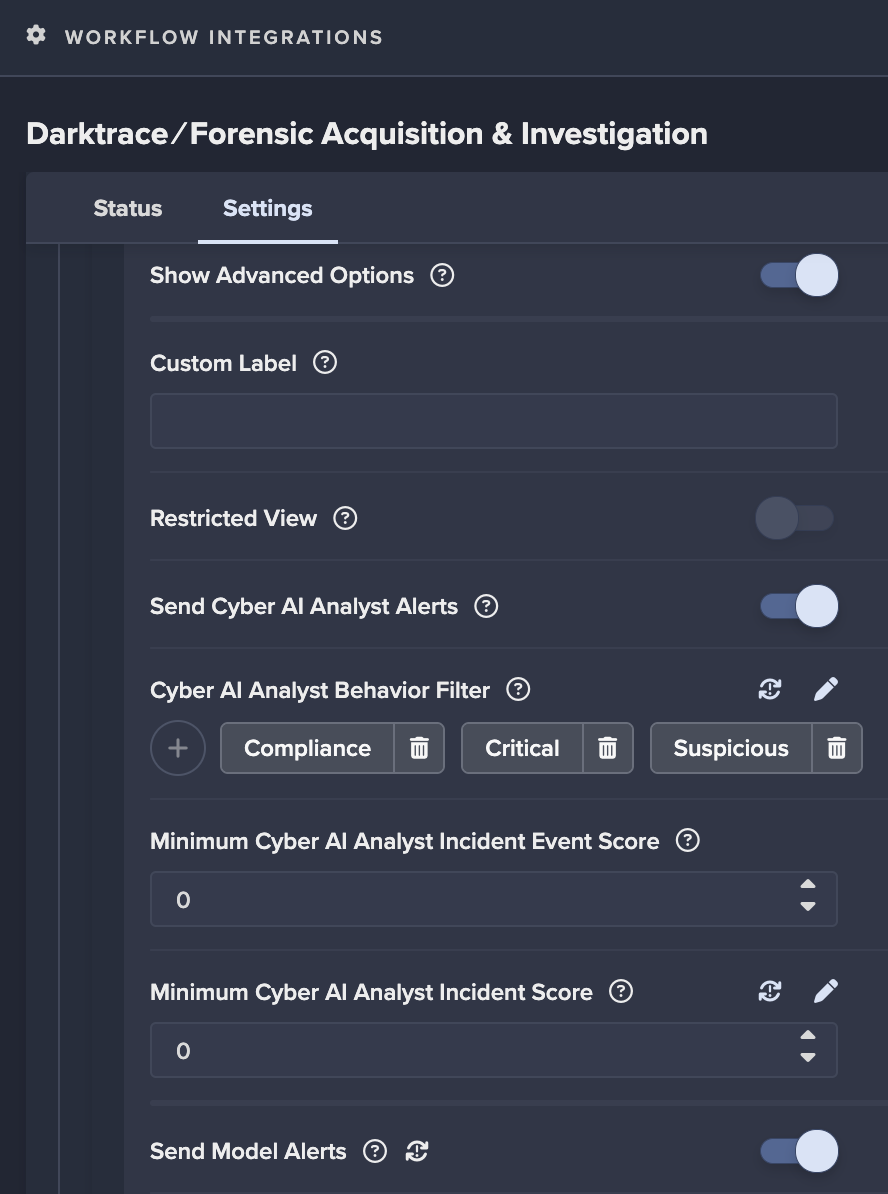
- You can configure the alerts sent at a more granular level using the advanced options. Ensure
Send Cyber AI Analyst AlertsandSend Model Alertsis enabled at a minimum.
- Click
Save - Click on
Verify alert settings
Manual Investigations
NOTE: In later Darktrace versions, the Forensic module can be automatically configured by enabling the 'Allow auto-configuration' setting. If this is not available to you, follow these steps:
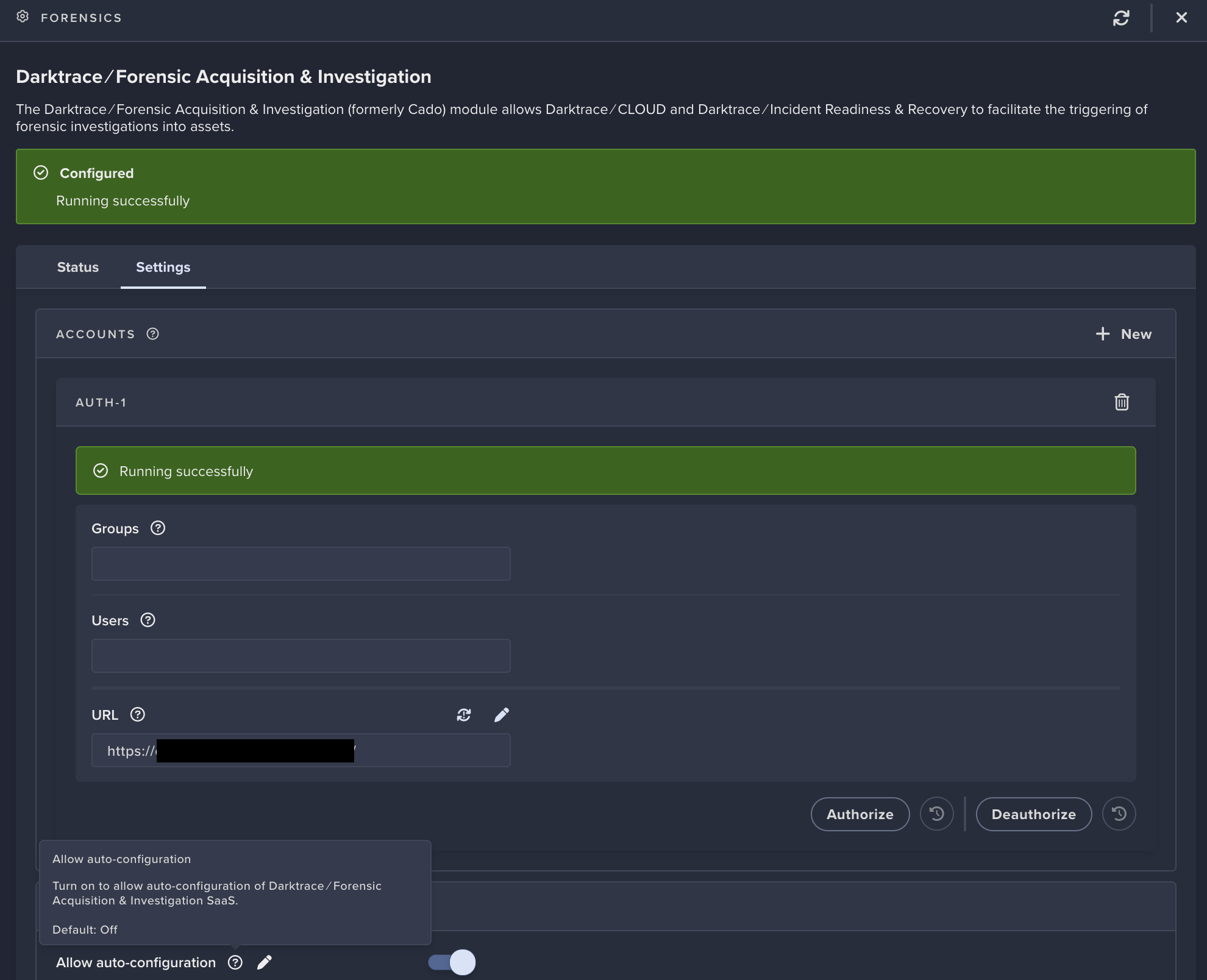
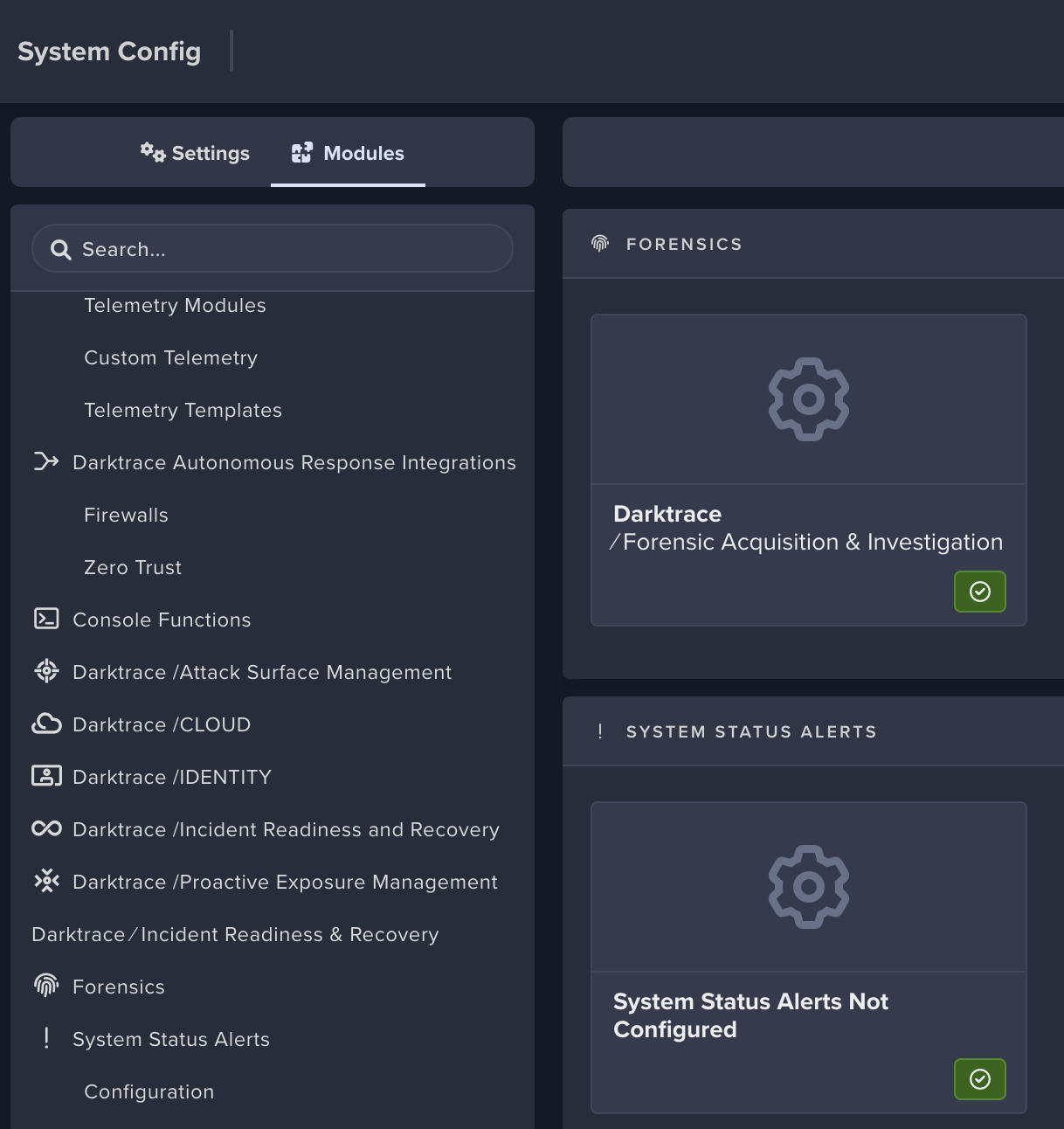
- To manually configure the
Forensicsmodule, close theWorkflow Integrationsscreen and selectForensicsmodule, then click on Darktrace /Forensic Acquisition & Investigation
- Select
Settings, then use the sameURLandAPI Keyfor the workflow integration in the form, then click onSave. Leave Groups, Users, and JWT fields blank.
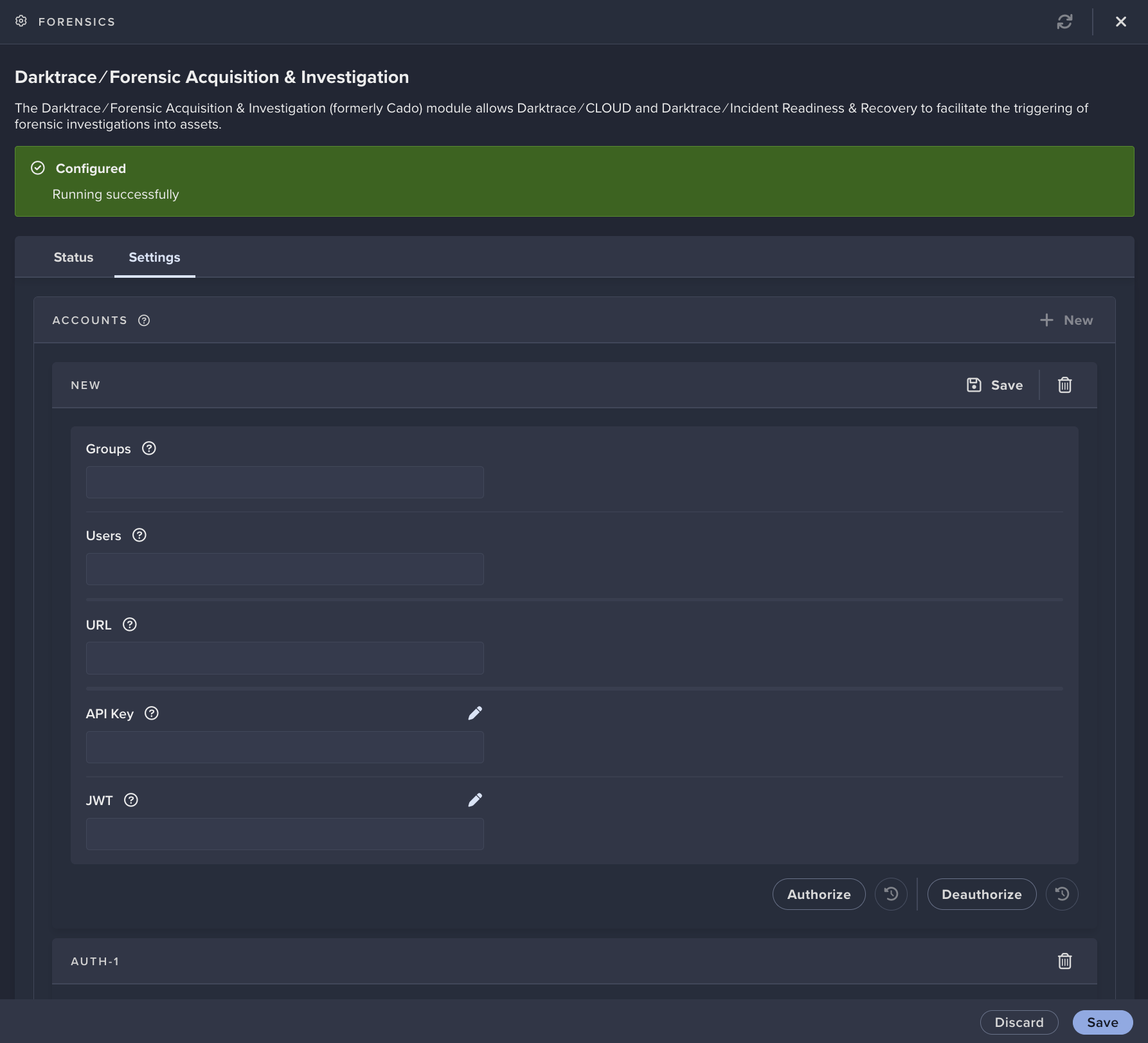
- Click on
Authorize