How to Use the / Forensic Acquisition and Investigation API
The / Forensic Acquisition and Investigation API allows third-party tools and automation scripts to interact seamlessly with the / Forensic Acquisition and Investigation platform. You can use the API, along with pre-built integrations, to perform tasks like:
- Triggering platform operations (e.g., acquiring instances from your cloud environments)
- Retrieving captured data (e.g., suspicious events)
- Managing and controlling investigations
- And more
This guide will walk you through the essential steps to onboard and integrate with the / Forensic Acquisition and Investigation API.
Creating and Storing an API Access Key
To access the / Forensic Acquisition and Investigation API, you’ll need to authenticate with a valid API Key. Follow these steps to generate an API Key within the platform:
- Navigate to Settings in the bottom-left corner, then click on the API tab.
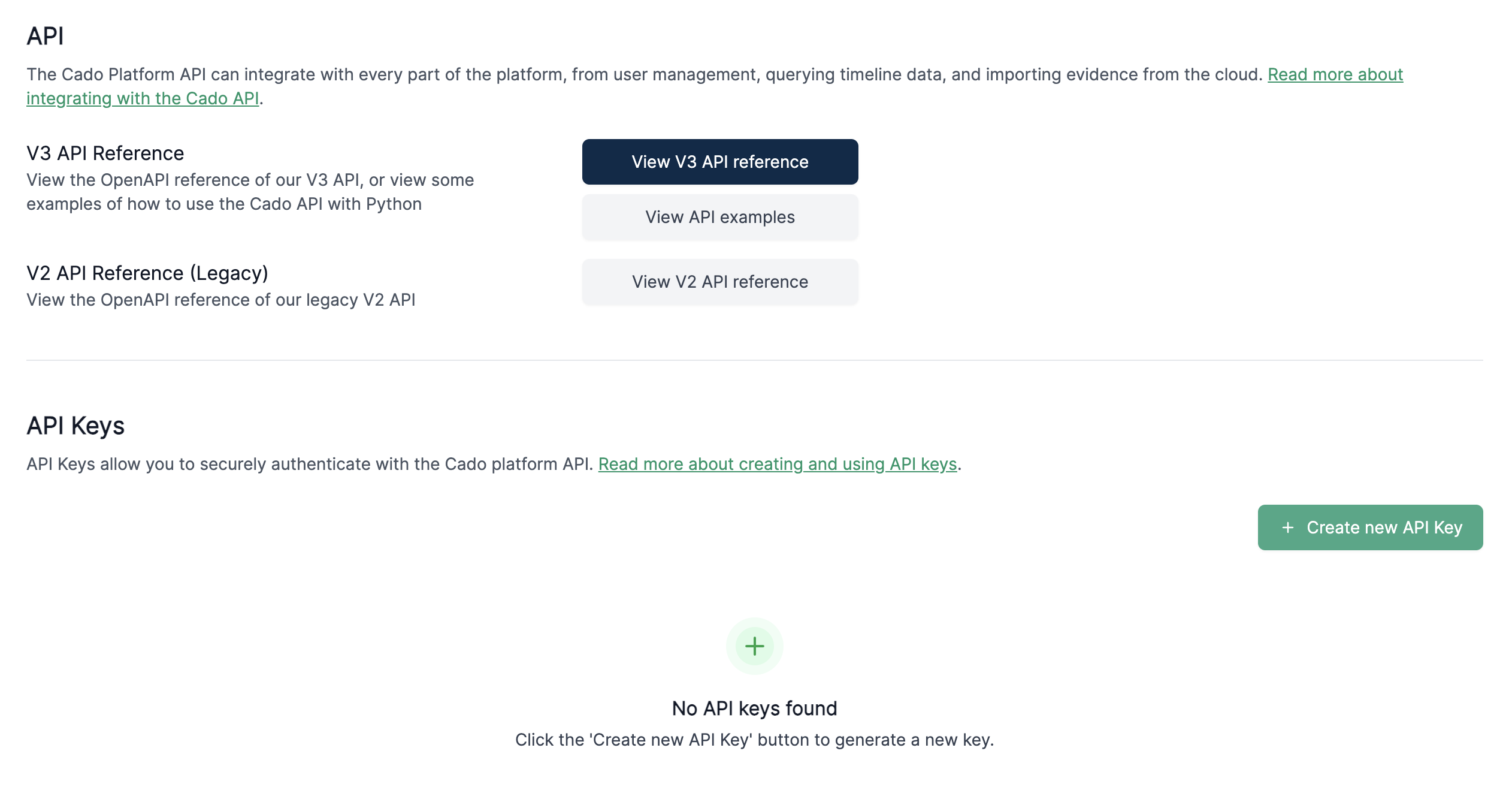
- Under the API Keys section, click the Create API key button.
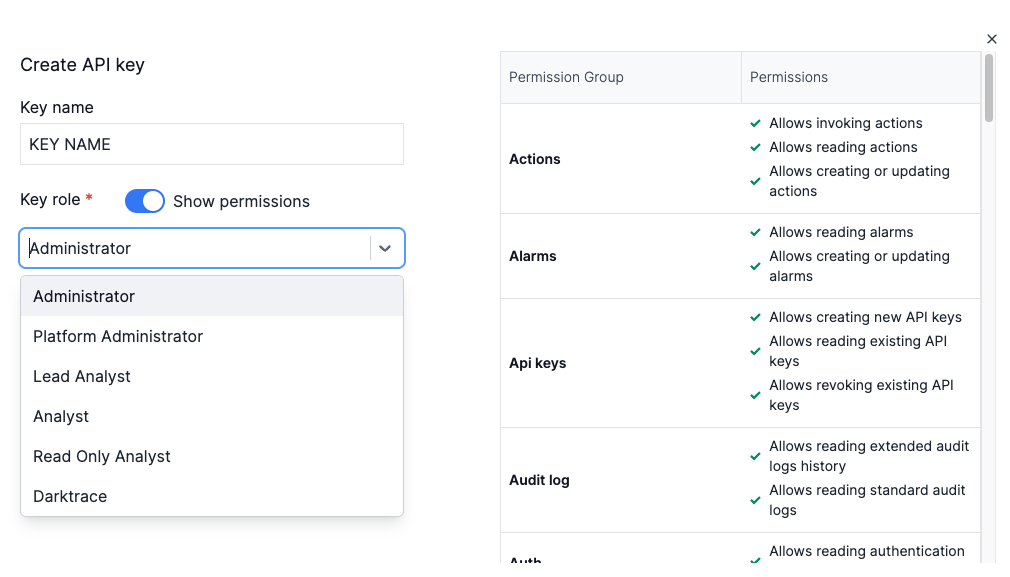
- Enter an optional key name
- Select a role from the dropdown and click Create
- Copy the Public Key. This key serves as the identifier for the API Key, which can be used later to revoke access if needed.
- Copy the Secret Key and store it in a secure location (e.g., a password manager). You will not be able to view the Secret Key again after closing the dialog. This key is required when integrating with third-party providers.
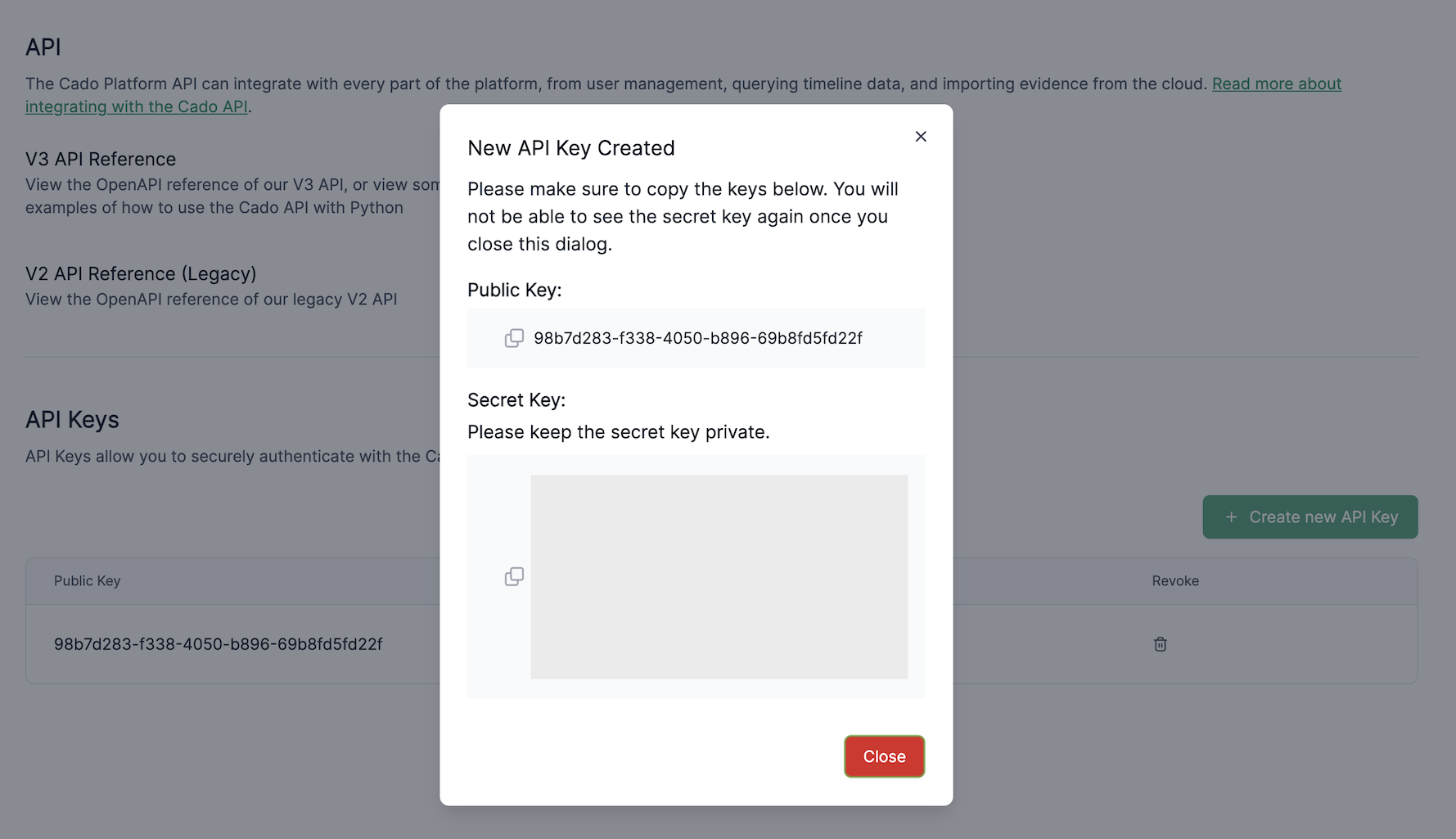
The Secret Key functions as the Access Token for authenticating your requests.
The Secret Key is shown only once. Be sure to save it securely, such as in a password manager.
Platform Base URL
In the following tutorials, the term "Platform Base URL" refers to the IP address or domain name where your / Forensic Acquisition and Investigation platform is deployed. For example:
https://ec2example.compute.amazonaws.com
Full API Documentation
You can find detailed API references and examples for versions V2 and V3 in the API settings page. Additional API examples are available on GitHub: https://github.com/cado-security/cado-api-examples