How to Export to SIEM
Security Information and Event Management (SIEM) tools provide real-time analysis of security events from applications and network devices. SIEM systems are essential for SecOps teams to correlate events, analyze logs across different systems, and manage security risks efficiently. By integrating the / Forensic Acquisition and Investigation platform with SIEM, you can leverage the power of both SIEM and / Forensic Acquisition and Investigations unique cloud-based forensic capabilities.
/ Forensic Acquisition and Investigation converts the processed timeline into two formats:
- CEF (Common Event Format): A widely recognized format for SIEM systems
- CadoJson: A custom JSON format optimized for certain SIEM systems like Splunk and Sentinel
Both formats are uploaded to the AWS S3 bucket and folder of your choice, and you can configure your SIEM system to automatically import these files.
Getting Started
To begin exporting timelines to your SIEM:
- Enable the SIEM integration by navigating to Settings -> Platform Settings -> Integrations -> SIEM.
- Set the desired S3 bucket and folder where the timeline files will be exported.
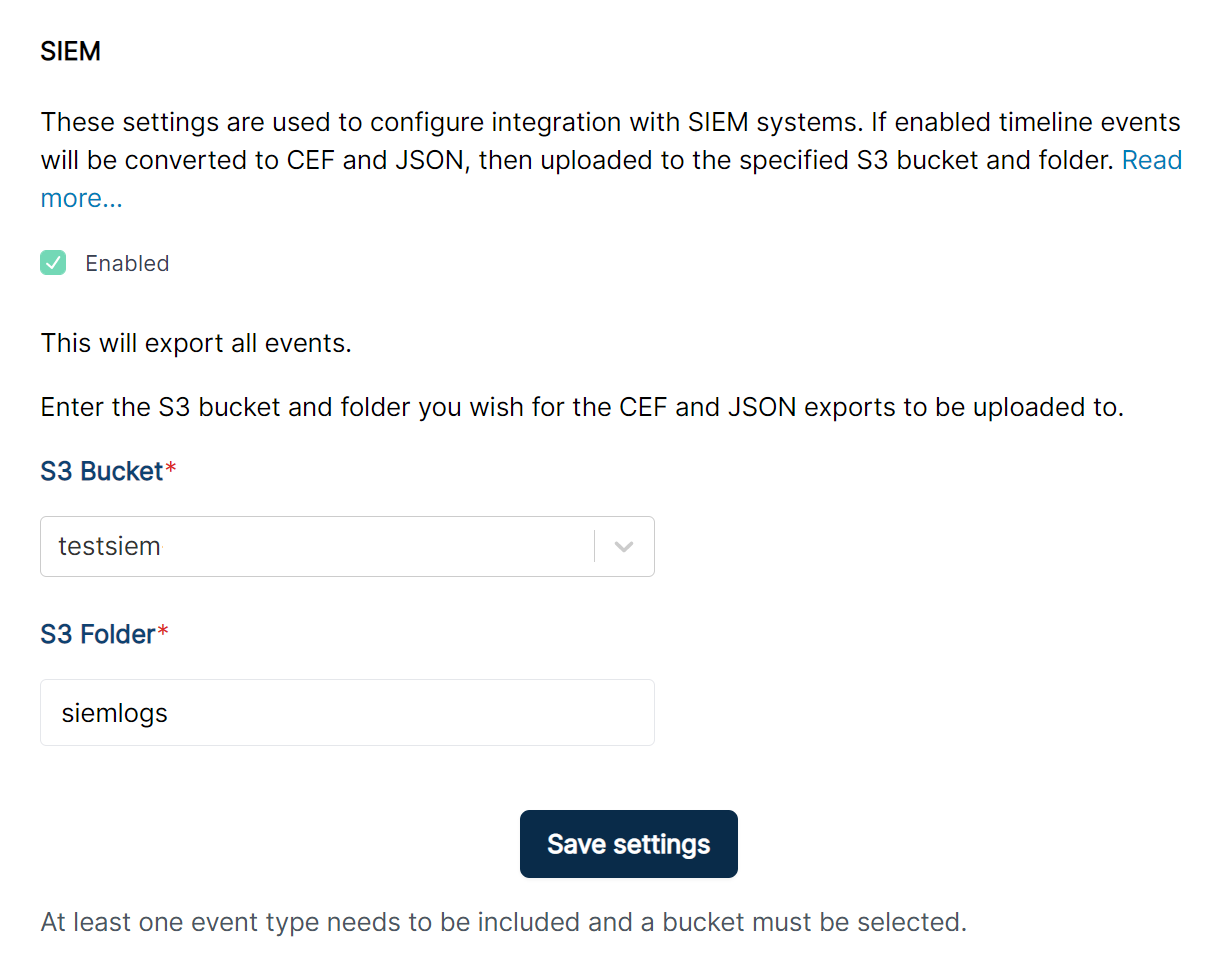
Once enabled, whenever you import evidence into / Forensic Acquisition and Investigation, the timeline will automatically be converted and uploaded to the specified S3 location. You will need to configure your SIEM to monitor this folder for new files and import them automatically.
Cado CEF Standard
Below is an example of a CEF log generated by / Forensic Acquisition and Investigation:
CEF:0|CadoSecurity|CadoResponse|1.0.2|0|Content Modification Time|10|alarm=True evidence_id=2 evidence_name=aws_compromise.zip macb=M... source=FILE eventTime=1595194940 filePath=/tmp/file.txt eventId=Q5FBqHwBX9dvp1T5IsHT msg=Malicious File Detected: cryptomining_malware_wannamine
The CEF log follows this standard format:
CEF:0|CadoSecurity|CadoResponse|Version|Signature ID|Name|Severity|Extension
The "Extension" part contains key-value pairs with additional fields, as detailed below.
CEF Extensions
| EXTENSION FIELD | EXAMPLE VALUE | TYPE | DESCRIPTION |
|---|---|---|---|
| eventTime | 890430600 | int | Unix timestamp of the event. |
| source | REG | str | Subtype of the event source. |
| sourcetype | LOG | str | Type of file or data producing the event. |
| type | Content Modification Time | str | Event type (e.g., Last Executed Time, Content Modification Time). |
| filePath | /Users/nromanoff/NTUSER.DAT | str | Path of the file linked to this event. |
| short | Executable in suspicious location | str | Summary of the event. |
| evidence_id | 1 | int | ID of the evidence item in / Forensic Acquisition and Investigation. |
| alarm_severity | 1 | int | Event severity (Malicious: 1, Suspicious: 3, Other: 10). |
| macb | .A.. | str | MACB (Modification, Access, Change, Birth) representation. |
| host | EC2AMAZ-T80EJE1 | str | Hostname linked to the event. |
| inode | 123 | str | Inode or file system identifier. |
| alarm | True | bool | Whether this event has an associated alarm. |
| sha256 | 9473976... | str | SHA-256 hash of the related file. |
CadoJson Format
The CadoJson format contains the same fields as CEF, represented in JSON structure. Here is an example:
{
"macb": "M...",
"source": "REG",
"sourcetype": "Registry Key",
"type": "Content Modification Time",
"host": "-",
"short": "[HKEY_CURRENT_USER/AppEvents/Schemes/Apps/.Default/Notification.Proximity] (empty)",
"inode": "-",
"sha256": "9473976b2769337ca9a7243bf1ceddb3335f9551e113240ebb0c53ae789878d5",
"eventTime": 1610559005,
"filePath": "/NTUSER.DAT"
}
Log Analysis Considerations between SIEM & Cado
For more information about how SIEM logs compare to Cado's forensic capabilities, refer to this guide.