How to automatically deploy a cross-account IAM Role in AWS
To automate the deployment of the IAM Policy and Role in multiple AWS accounts within your organization, you can use AWS CloudFormation StackSets. This method allows you to deploy the necessary IAM roles and policies across all target accounts in your organization.
More information on CloudFormation StackSets can be found here: Working with AWS CloudFormation StackSets.
How to add AWS Account
The new AWS deployment method enables you to automatically onboard a cross-account role from the / Forensic Acquisition and Investigation UI, offering a more automated and streamlined experience.
-
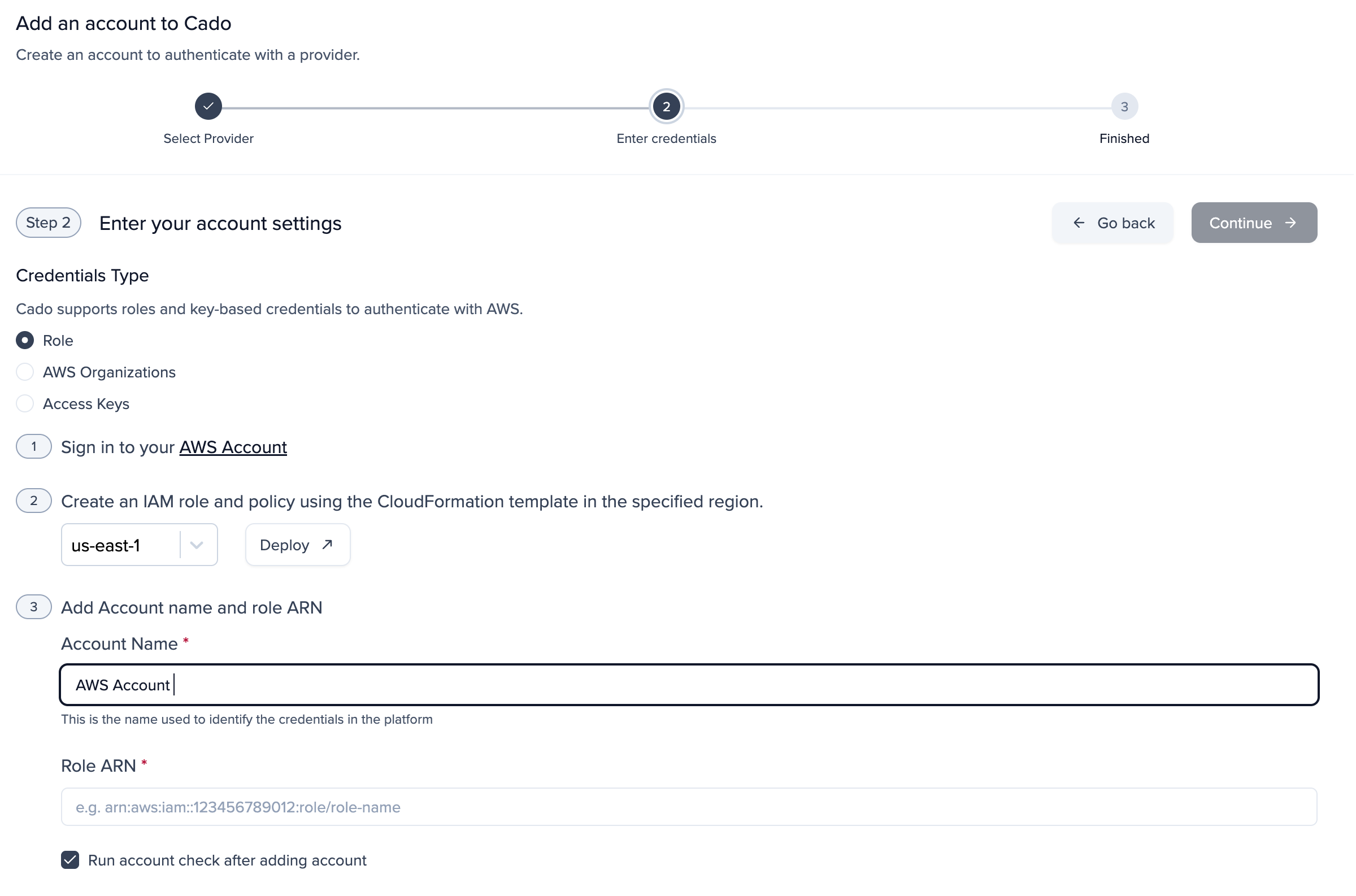
In Settings go to the Accounts tab and click Create an Account then select AWS.
-
Sign in with your AWS Account
-
Create an IAM role and policy using the CloudFormation template in the specified region
-
Add Account Name and Role ARN
-
Select if you want to run an Account Check after adding account
Steps to Deploy the IAM Policy and Role using CloudFormation StackSets
-
Open StackSets
From your master StackSet account (the account enabled to deploy resources into other AWS accounts), navigate to "StackSets." -
Create a New StackSet
Click Create StackSet. -
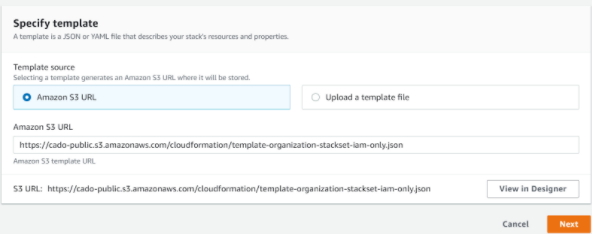
Enter the CloudFormation Template URL
Enter the S3 URL for the CloudFormation template:https://cado-public.s3.amazonaws.com/cloudformation_v2/StacksetCrossIAM.yamlThen, click Next.
-
Proceed Through the Setup
Click Next through the following configuration steps. -
Select Region
Under "Create StackSet," select any region (IAM roles are global, so this can be any region).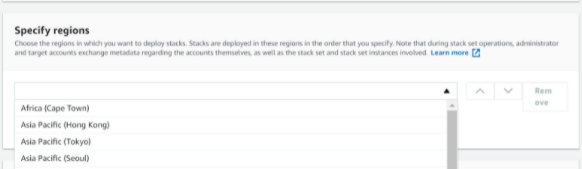
-
Deploy the StackSet
Once deployed, this will create the required IAM Policy and IAM Role in each target AWS account. You can verify the role and policy by navigating to IAM > Roles in the target AWS accounts.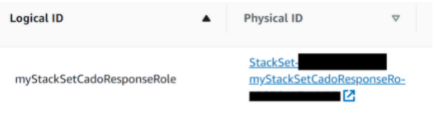
After deploying the cross-account IAM roles, you will need to add the newly created Role ARN to the platform. Follow the steps outlined here, or to automate this process, refer to Automating Cado Cross-Account Creation.
Automating Cross-Account Addition in / Forensic Acquisition and Investigation
Once the cross-account IAM role is created, the next step is to add the IAM Role ARN to the platform. This enables access to the target AWS accounts within Cado.
To automate this process via the / Forensic Acquisition and Investigation API, see the example script for adding AWS credentials in the platform:
Example API Script for Adding AWS Credentials.