How to Import Azure Kubernetes Service (AKS) Containers
The / Forensic Acquisition and Investigation platform allows you to collect key logs and forensic artifacts from containers running in Azure Kubernetes Service (AKS).
Known Limitations
- / Forensic Acquisition and Investigation can acquire artifacts from containers built with distroless containers using / Forensic Acquisition and Investigation Host only. Containers with the
gcr.io/distrolessimage tag will be hidden. For more details, see Kubernetes Deployments. - / Forensic Acquisition and Investigation will hide pods running under the following namespaces, which are generally system-level namespaces running a distroless environment:
kube-system,kube-public,kube-node-leasegke-gmp-system,aks-commandgmp-system,calico-system,tigera-operator
Import Steps
-
Navigate to Import > Cloud.
-
Select the Azure credentials configured under Azure > Cross Subscription and Tenancy.
-
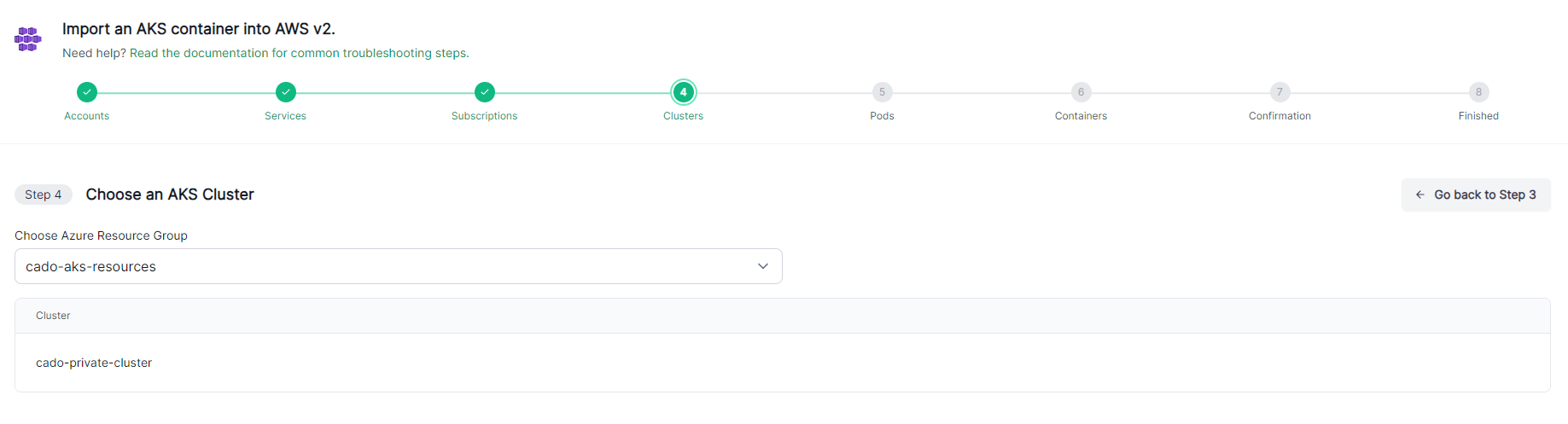
Choose the resource group associated with the AKS cluster.
-
Follow the steps to select your Cluster, Pod, and Container.
-
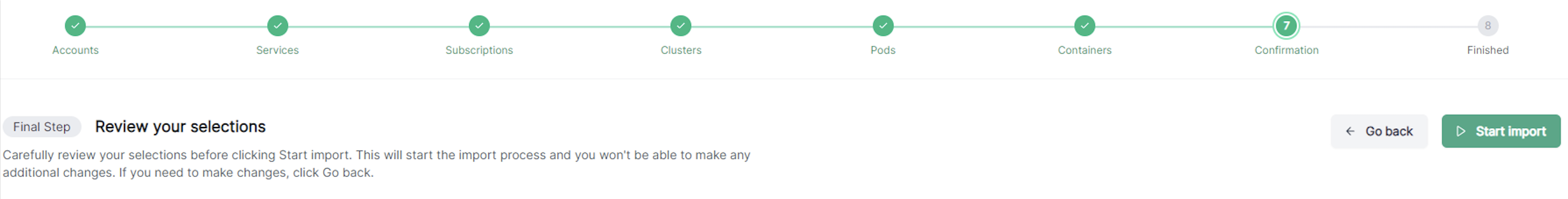
Confirm the details and click Start Import.
/ Forensic Acquisition and Investigation will automatically collect all key logs and forensic artifacts from the container for investigation. For most acquisitions, the import and processing will take just a few minutes to complete.
Private Cluster and AAD-backed Cluster Support
The / Forensic Acquisition and Investigation platform supports capturing data from AKS Private Clusters and AAD-backed Clusters. This functionality is achieved using the Azure Command Invoke APIs.
There are two key considerations with this method:
- Capturing from private or AAD clusters is significantly slower than from a public cluster.
- The Azure API spins up a pod within the cluster to execute / Forensic Acquisition and Investigation Host. Ensure that your cluster has enough resources and nodes to schedule this command pod.
The newly created pod will automatically shut down and remove itself after 1 hour.
For AAD-backed Clusters, the Azure Kubernetes Service RBAC Cluster Admin role assignment will need to be added to the / Forensic Acquisition and Investigation role assigment in the Azure RBAC. This role assignment will need to be added at the cluster-resource level (i.e. go to your cluster in the Azure portal -> Access Control (IAM)). For more information, please follow the Microsoft Azure documentation.
Scoping Down the Role for Access to AKS
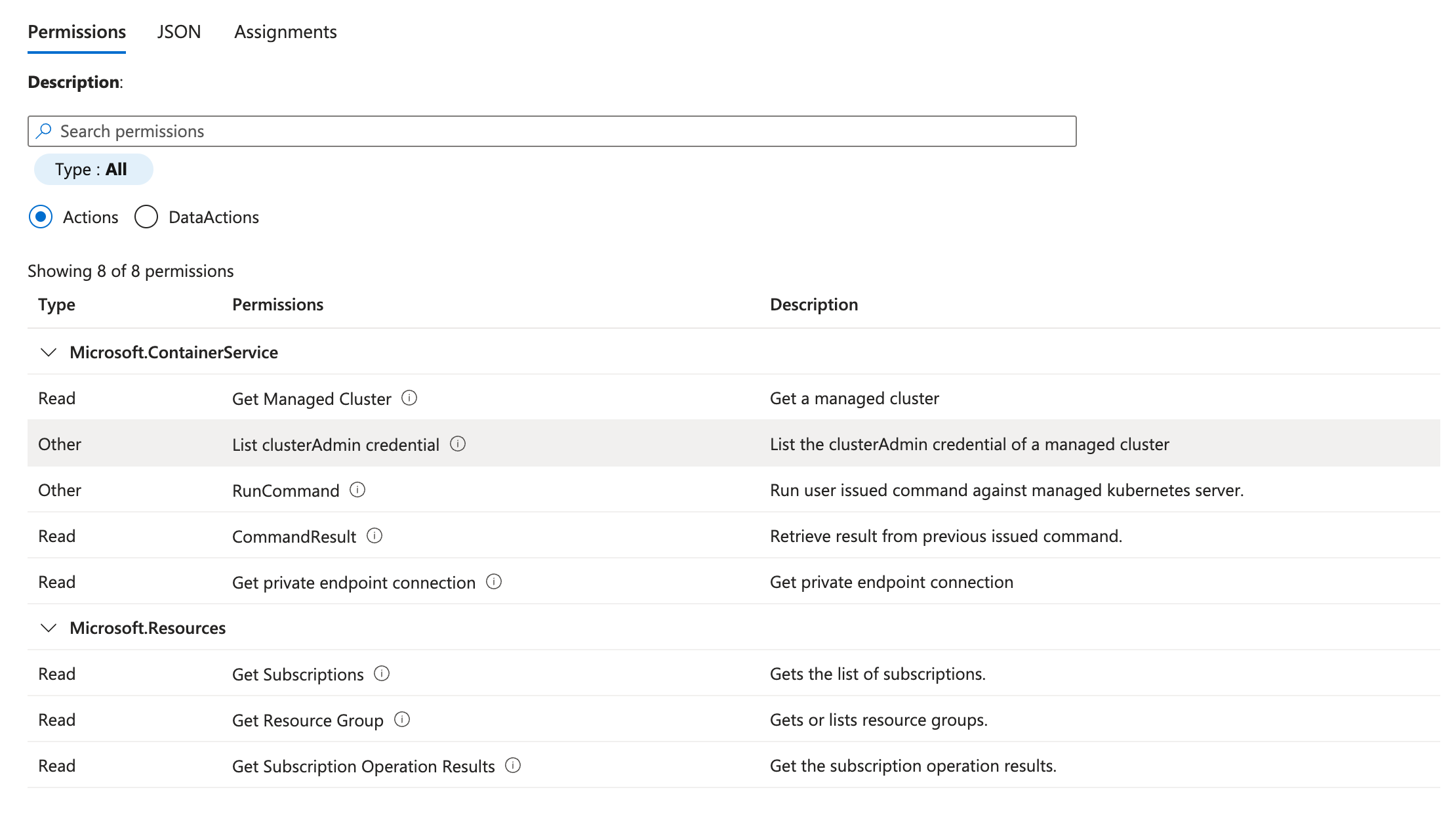
The / Forensic Acquisition and Investigation platform requires specific permissions to access and execute code in containers. You can use the following role definition to limit the permissions required for / Forensic Acquisition and Investigation to access and acquire data from AKS:
{
"id": "",
"properties": {
"roleName": "ScopedDownAKSTest",
"description": "",
"assignableScopes": [
""
],
"permissions": [
{
"actions": [
"Microsoft.Resources/subscriptions/operationresults/read",
"Microsoft.Resources/subscriptions/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.ContainerService/managedClusters/read",
"Microsoft.ContainerService/managedClusters/runCommand/action",
"Microsoft.ContainerService/managedClusters/commandResults/read",
"Microsoft.ContainerService/managedClusters/privateEndpointConnections/read",
"Microsoft.ContainerService/managedClusters/listClusterAdminCredential/action"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}